Working with Tailscale#
Tailscale is a VPN service that is designed to be easy to use and secure. It is a great tool to connect your devices together and access them from anywhere. However, Tailscale may conflict with Surge(VIF mode) because both service will create a tun interface to take over the traffic. Most of the time, they work together without any problem. But sometimes1, it breaks the things and is hard to debug.
Tailscale: A brief look#
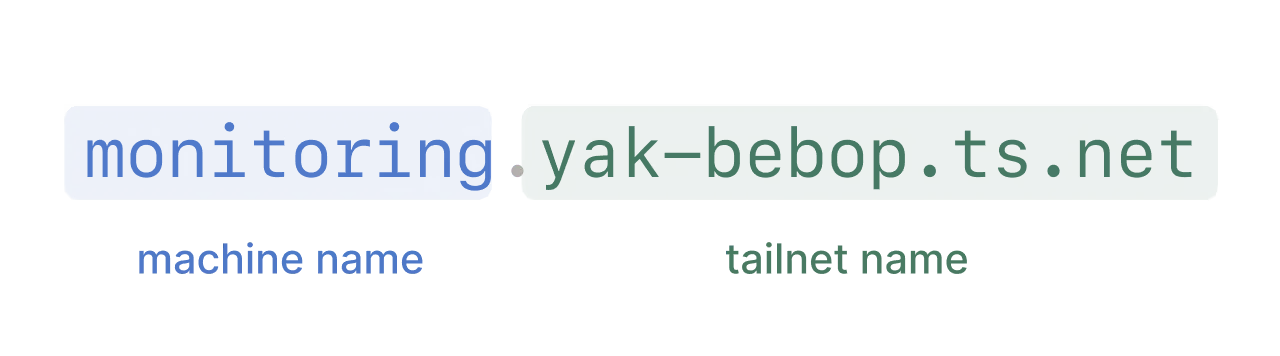
Tailscale connect each device by assigning a unique IP address in the range of 100.64.0.0/10 and Tailscale will also assign some convenient DNS shorthand for the device. For example, <machine-name>.<tailnet-name>, and Tailscale has its own DNS server to resolve these DNS queries (called MagicDNS).
Solving the conflicts#
To solve the problem, we need to:
- Redirect all
100.64.0.0/10traffic to the Tailscale interface - Resolve some DNS queries to the Tailscale DNS server
In Surge, we can create a proxy that points to a specific interface:
[Proxy]Tailscale = DIRECT, interface = <tailscale-tun-interface>And the redirection can be archived by creating a routing rule:
[Rule]IP-CIDR,100.64.0.0/10,Tailscale,no-resolveAs for the DNS resolution, we can also create a rule to resolve the DNS queries to the Tailscale DNS server:
[Host]*.ts.net = server:100.100.100.100You need to disable Use Tailscale DNS setting in the Tailscale panel to make it work.
This prevents Tailscale from overriding the DNS settings.
The Tailscale DNS server (100.100.100.100) will be up once you click the Connect button.
Footnotes#
-
I have observed that if Tailscale and Surge (VIF) mode are enabled at the same time, docker will fail to pull images. The TLS connection will just timeout. In the further investigation, I found that it might be caused by the Tailscale DNS configuration. ↩